Reverse Engineering (RE) is one of the hard category in Capture The Flag competition. So today, I want to share some tips on Reverse Engineering in CTF competition. Firstly, let to be honest. I’m a very noob, newbie and beginner in RE. These tips I got from various of web blog that I compiled it then make note for me. So, here some of it. Check it out.
-
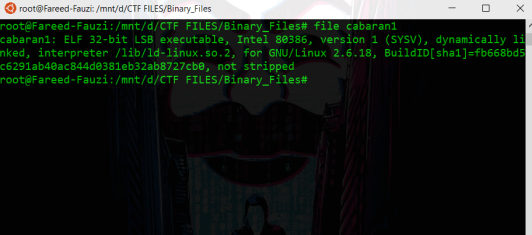
Whenever you get a file, issuing
file [filename]command first to it to know what really file is it.
-
Checkout the EXIF data of the file by using
exiftool [filename]command. -
Use
strings [filename]command to read the strings in the binary. -
Maybe some
grep -icommand too. -
You need know about Assembly Language and computer architecture for this challenge!
-
Note the flag at one text file.
-
PE file
-
ELF File
-
APK File
-
.NET File
-
Java file.
-
PE File
-
Use
strings [filename]command to read the strings in the binary. -
Maybe some
grep -icommand too. -
Use DIE, PEID, PEBear, or PEView software to do static file analysis. Find details of file in there!
-
Use HxD to check the header file, file signature. Maybe the corrupt file sign one.
-
Find it whether it packed or not. Find online unpack.
-
Find it whether the binary has anti-debug or not.
-
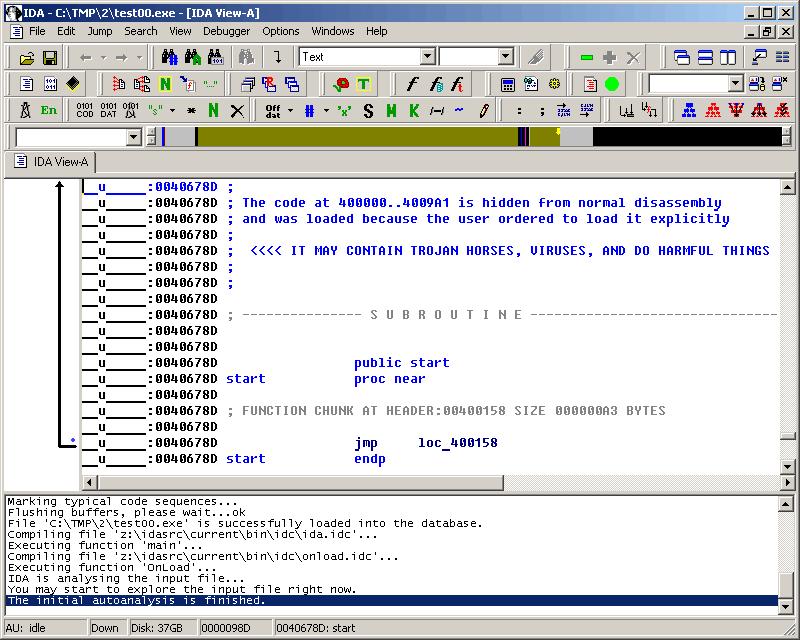
Use IDA Pro software to perform static analysis on the binary. IDA is one of the popular disassembler tool out there. You should try it!

This interface is IDA Pro with black theme. 😉 -
When do analysis static or dynamic focus on strcmp, function call, conditional jump.
-
Use Snowman software to perform decompiler.
-
Use debugger like Immunity Debugger, x64Dbg/x32Dbg, or WinDbg to debug the binary.
-
Scan the binary on virustotal.com to know something malicious.
-
run command
rundll32 [filename] -
Use eXeScope to find out about header, import and resource of the binary.
-
Use universal extractor to extract files in the binary.
-
-
ELF File
-
Use
strings [filename]command to read the strings in the binary. -
Maybe some
grep -icommand too. -
Use DIE on the binary.
-
Find it whether it packed or not. Find online unpack.
-
Find it whether the binary has anti-debug or not.
-
Use HxD to check the header file, file signature. Maybe the corrupt file sign one.
-
Use
ltrace ./[filename]command to know what library function are being called in the binary. -
Use
strace ./[filename]command to know what system and signal function are being called in the binary. -
Use
nm [filename]command to know what symbol being called in the binary. -
Use
readelf -a [filename]command. It will displays information about ELF files. -
Use IDA Pro software to perform static analysis on the binary.
-
Use Snowman software to perform decompiler.
-
Use debugger like GDB-Debugger to debug the binary.
-
-
APK File
-
Use
APKTool [filename]command tools. -
Use Android Emulator to run the program.
-
Use Android Debug Bridge.
-
Use
dex2jar [filename]command tools. -
Use jd-gui.
-
-
.NET File
-
Use dnSpy software. Very powerful. Edit it -> compile -> save all. Try run the program back!
-
-
Java file
-
Use Java Decompiler program to decompile it.
-
Author: Fareed Fauzi

Bach. Network Technology, FSTM KUIS.
My name is Fareed. Currently study Computer Networking. Passionate in Reverse Engineering, Malware Analysis and Pentest. Oh also, teh tarik lover (that’s why malaysian ramai tembam 😛 ) and Chelsea supporter.
Other articles you might interested;
- Original article: https://fareedf.wordpress.com/2018/09/02/ctf-reverse-engineering-tips/
- https://fareedf.wordpress.com/2018/09/02/ctf-unikl-2018-writeup-stega-1/
- https://fareedf.wordpress.com/2018/09/02/crackmes-one-writeup-sh4ll1/
- https://fareedf.wordpress.com/2018/09/02/ctf-unikl-2018-writeup-mr-cool/
- https://fareedf.wordpress.com/2018/09/02/ctf-unikl-2018-writeup-nexagate-bounty-2/